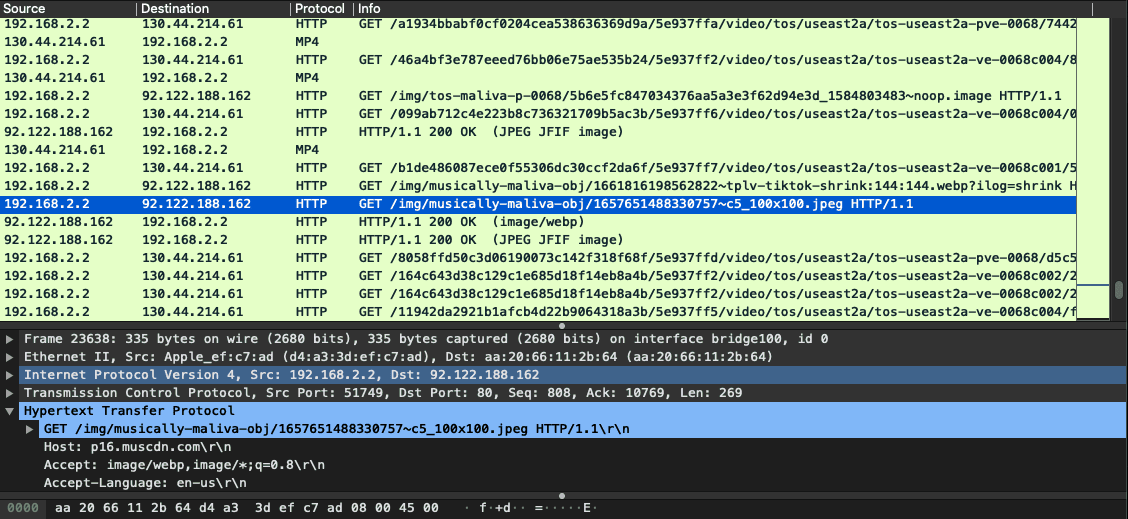
Not just interception, but also manipulating.
Tommy Mysk and Talal Haj Bakry, two developers who first revealed this issue, has also detailed in their blog. The due claims the vulnerability in TikTok lies with its transportation of content via an unsecured protocol called HTTP. This was later developed to HTTPS (S stands for Secure) for being more secure. Usage of HTTP may let the content pass faster but at the cost of the app’s security. Like many others, TikTok uses a CDN for rerouting the users content around the world in a faster manner, but doing it on HTTP lets any middleman as ISP, government, hackers etc to snoop on what’s being shared easily. They can even intercept the communications easily and, as the duo claimed, can replace a certain account’s videos with other videos procured from other accounts. To make this belief, they’ve even illustrated an intercept into TikTok’s traffic and manipulated the content of the official WHO’s account! They posted a video showing misinformation about COVID-19, which can potentially be seen and fooled followers. They said the problem existed with TikTok iOS v15.5.6 and Android v15.7.4, which are still using unencrypted HTTP standards!
To note, TikTok’s having an active user base of 800 million monthly. It’s even rivaling against YouTube, world’s popular video sharing platform. And with such popularity, TikTok is expected to maintain strict security protocols, as any misinformation spread from official accounts as demonstrated by the duo could create havoc in public. Source: Mysk Blog