Vulnerable Subdomains
Microsoft Teams have garnered a significant number of users to be the desired target for hackers. It’s expected that after Zoom being hit with many privacy and security allegations, other working tools like Teams are expected to resolve any active loopholes. But the Microsoft Teams software in web and desktop versions is having a simple vulnerability that would let hackers compromise user accounts. As reported by CyberArk to Microsoft’s Vulnerability Disclosure Program, compromising the subdomains of Teams could give access to accounts and can impersonate the victim. This starts with an image being sent to the target, which should be opened (downloaded) in either of the two subdomains.
aadsync-test.teams.microsoft.com data-dev.teams.microsoft.com
These two are the subdomains of teams.microsoft.com, which are from desktop and web versions. Luring the target to download the image would send details of his account’s authentication tokens like authtoken and skypetoken. Obtaining these two are crucial for the attack.
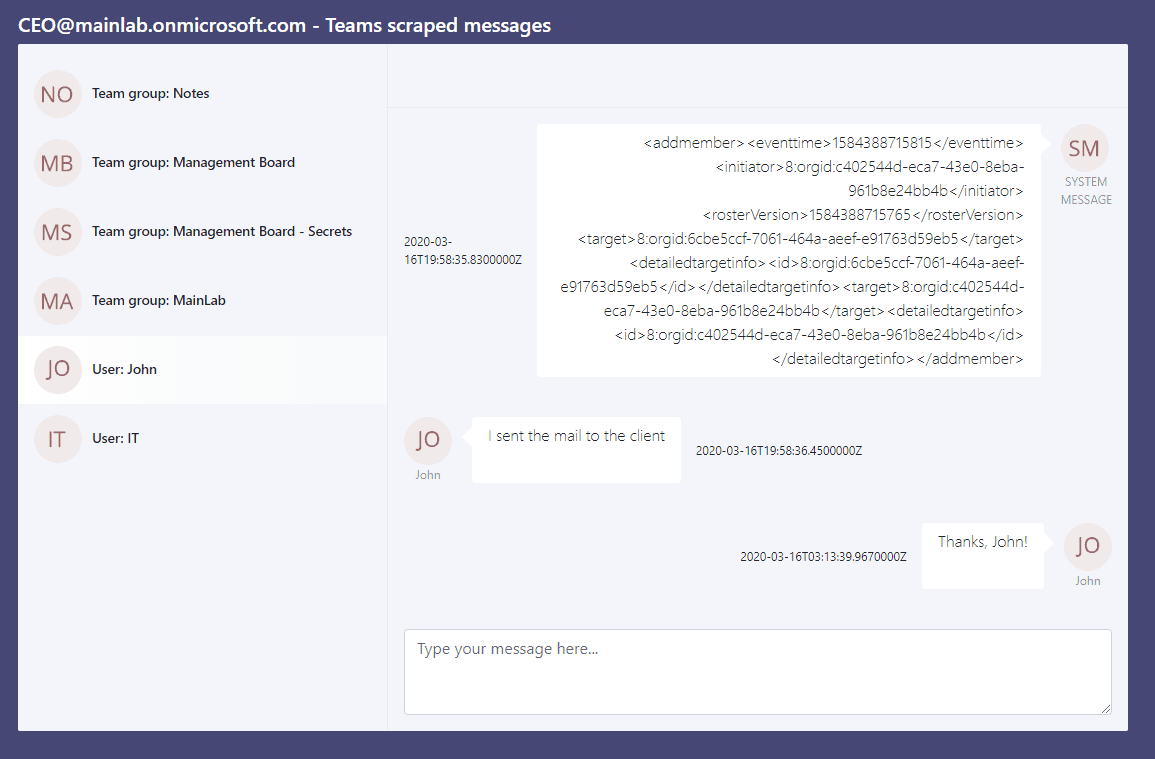
Obtaining Tokens From Image
The authtoken is used for authenticating images loading across Teams subdomains in desktop and web versions, and also to produce the skypetoken. The skypetoken will be used for authenticating the server that handles reading/writing requests from the client. An attacker here needs these two tokens and a digital certificate to pull the hack. And obtaining them is easy by subdomain takeover attack and a simple digital certificate. The security researchers have demonstrated the attack by creating an image to fool users and obtain tokens. These are then used to take over his account and read/write messages throughout his network. On his behalf, the attacker is even privileged to make calls too. Microsoft has erased the misconfigured DNS records to avoid those subdomains being compromised. And other measures were taken to avoid this trick in the future. Source: SecurityTrails